.NET Software Composition Analysis
- What is Software Composition Analysis (SCA)?
- Software Composition Analysis on .NET Application
- NDepend Software Composition Analysis Rules
- Detecting when a Package or an Assembly is Referenced in Multiple Versions
What is Software Composition Analysis (SCA)?
Software Composition Analysis (SCA) is an automated approach used to identify open-source components within a codebase. It assesses these components for security vulnerabilities.
In today’s DevSecOps workflows, SCA has become essential. By integrating SCA testing early and continuously, development and security teams can maintain high productivity while upholding robust security and code quality standards.
SCA is essential for mitigating security risks posed by third-party code in applications. Therefore, incorporating an SCA tool into security scanning and software development workflows is vital for organizations utilizing third-party libraries.
Why is Software Composition Analysis Essential?
The importance of SCA lies in the security, efficiency, and dependability it provides. With the overwhelming volume of open-source software in use today, manual tracking is no longer practical or scalable. The rise of cloud-native architectures and increasingly complex applications underscores the need for effective and reliable SCA solutions.
As development accelerates with the widespread adoption of DevOps practices, organizations require security measures that can keep pace without hindering productivity. Automated SCA tools fulfill this need by seamlessly integrating into development workflows to ensure secure and efficient progress.
Software Composition Analysis on .NET Application
In the context of a .NET application, Software Composition Analysis consists of analyzing both:
- The versions of NuGet packages and assemblies referenced by the application. This includes the .NET Base Class Library reference and other Microsoft libraries, which are not immune to security vulnerabilities.
- The versions of NuGet packages and assemblies referenced by NuGet packages and assemblies referenced by the application (transitive analysis).
NDepend Software Composition Analysis Rules
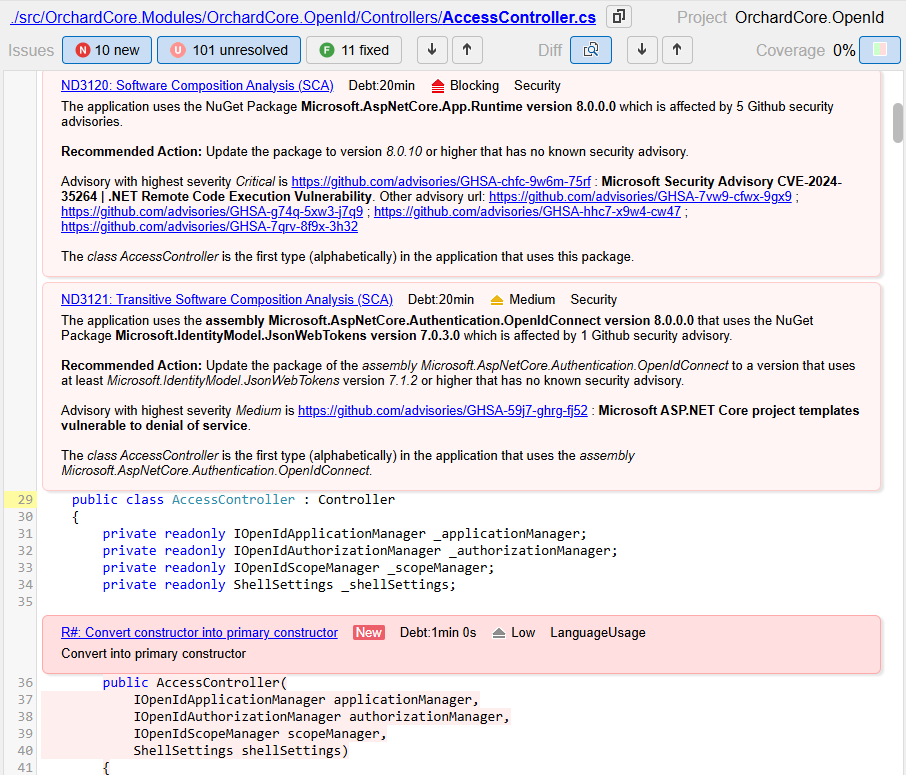
Since NDepend version 2025.1 two rules in the category Security are proposed:
- Software Composition Analysis (SCA) [ND3120]
- Transitive Software Composition Analysis (SCA) [ND3121]
These rules analyze the application and third-party assembly references against the Github Security Advisories on NuGet packages database.
A detailed explanation with recommended action is generated for each issue. The recommended action often consists of upgrading the referenced component to a version that addresses known security vulnerabilities.
Detecting when a Package or an Assembly is Referenced in Multiple Versions
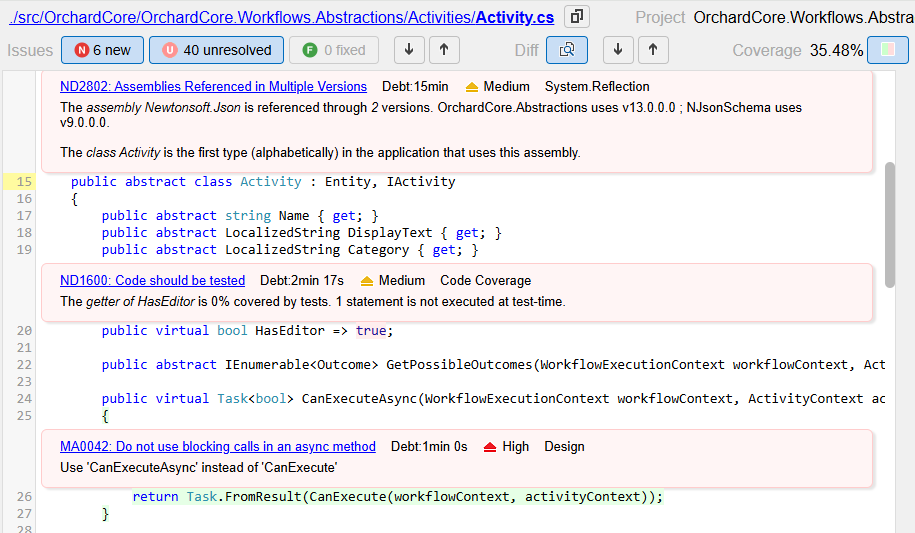
Related to SCA, the rule Assemblies Referenced in Multiple Versions [ND2802] can detect this situation.
A detailed explanation with the assemblies referencing the multiple versions is generated for each issue.